Marcus Hutchins, aka Malwaretech & VinnyK, the 25 year old former hacker who ‘accidentally’ stopped the WannaCry cyber-attack in 2017, and was subsequently arrested in the US for his role in creation and selling of the Kronos and UPAS Kit banking malware, will not be going to jail, he was told in sentencing today. He had potentially faced a 10 year stretch and a maximum US$ 500,000 fine.
He registered a domain name to understand the spread of the virus, but it halted the spread. Then in August 2017, after attending Def Con cyber-security conference in Las Vegas that summer, he was arrested by federal marshals at the airport before he was able to return to the UK, and had been in the US on bail since then.

Initially Hutchins initially plead Not Guilty in relation to hacking activities in 2012 and 2015 but online chats intercepted by the FBI on November 2014 provided a range of evidence including a complaint that he had only made US$ 8,000 from five sales of Kronos. He subsequently put in a guilty plea to two counts of creating and selling the malware and eight remaining charges were dropped.
US prosecutors argued that despite Hutchins having admitted guilt, apologising for and regretting his earlier actions, and having clearly reformed to work on the side of cyber-security, he still bore responsibility for his actions.
Hutchins said: “I regret these actions and accept full responsibility for my mistakes. Having grown up, I’ve since been using the same skills that I misused several years ago for constructive purposes. I will continue to devote my time to keeping people safe from malware attacks.”
Presiding judge JP Stadtmueller accepted that Hutchins had “turned a corner” and in a Milwaukee federal court today he sentenced Hutchins to one year of supervised release and he would be allowed to return to the UK and would not have to pay any fines.
Who is VinnyK?
The name VinnyK is of interest: it’s attached to early sales and scam claims around Kronos on Exploit.in. The earliest known post on the site relating to Kronos is from VinnyK and is in Russian, dating back to June 10 2014, as noted on Beaumont’s post regarding his concerns around the case against Hutchins and a malware blog. VinnyK was selling the malware for $3,000 back then. A month later, he was showing off how well Kronos fared against anti-virus systems. (The U.S. indictment against Hutchins only covers activity between July 2014 and July 2015.)
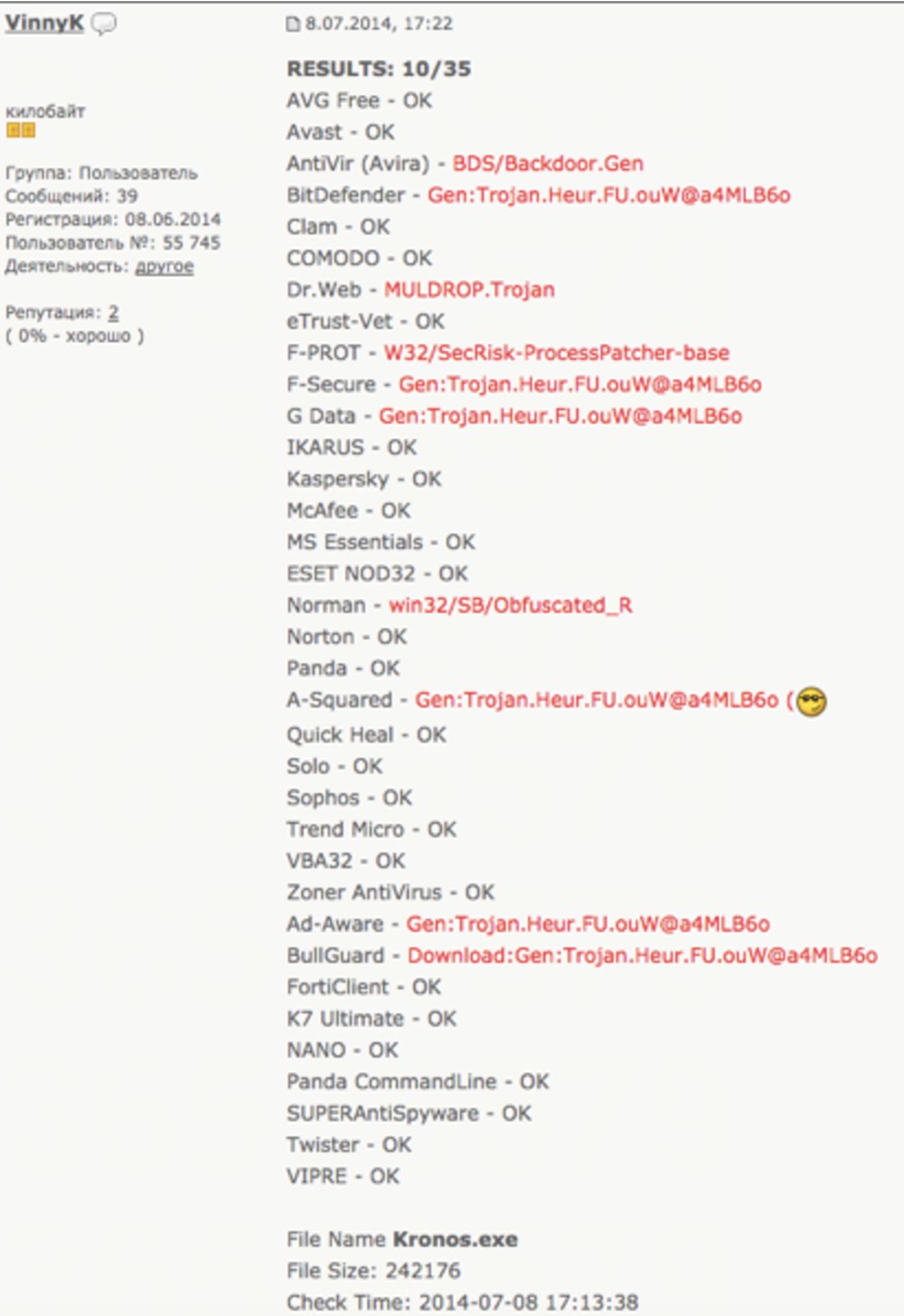
In another Exploit.in post, a review of the Kronos malware gets a three out of five. VinnyK responds by telling them updates to improve the tool were on the way.
But somewhere along the line, certain deals went sour. Publicly available posts from 2016 on the forum detail a $5,000 sale of an exploit kit to assist with a working Kronos botnet, in which the customer claimed to have been ripped off, to which VinnyK responded by vehemently defending his actions. The dispute came to an apparently amicable end with VinnyK returning the funds.
It’s apparent from the profile image of VinnyK that the user was eventually banned from the space after being declared a ripper. This could well be the coder Passworded was referring to.
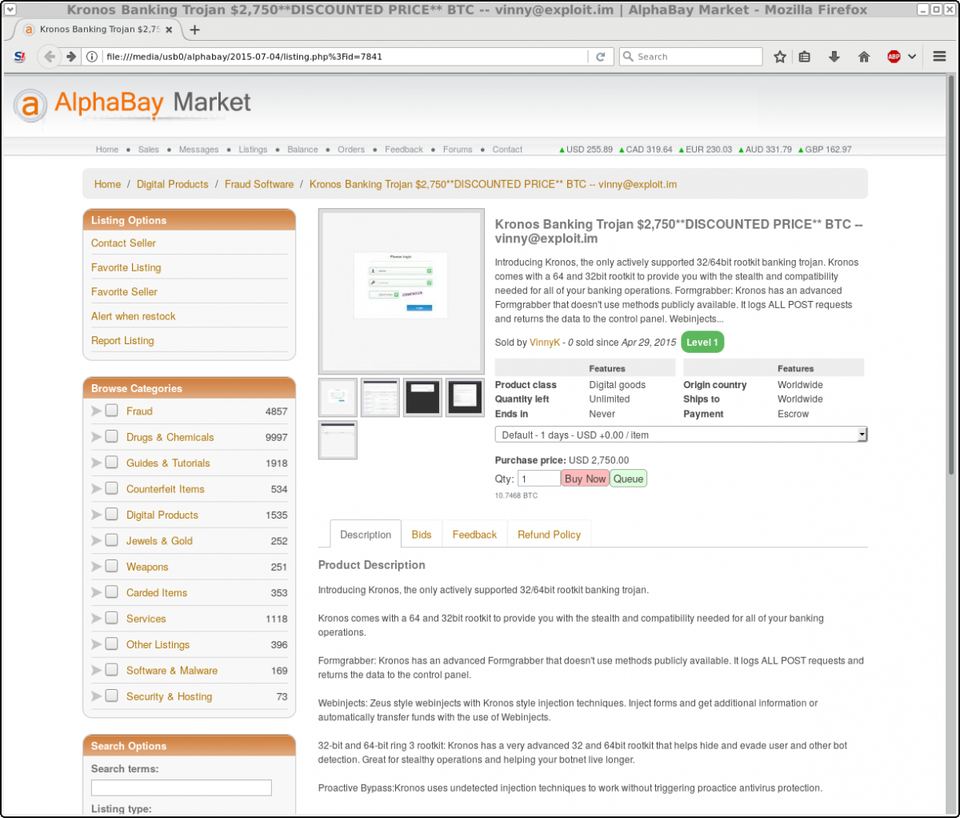
An advertisement for Kronos was placed by VinnyK on AlphaBay, the dark web market shut down in a major law enforcement action. The indictment claimed an unnamed party tried to sell Kronos on AlphaBay on or around April 29 2015, matching the date on the ad. The advertisement offers the malware for $2,750, cut from the original $3,000 price, but it had achieved no sales by July 4 2015, the time of the scrape, provided by Greg Jones of F-Secure’s Digital Assurance business. Again, VinnyK was the dealer, making it highly likely he’s the censored individual in the government charges.
Damage Done By Kronos
The lack of sales, reduced prices and alleged scams hint at another truth about Kronos: it was largely a failure amongst serious cybercriminals. There was early anticipation in 2014 it could go big, as prolific and profitable as one of its forbears, the banking malware known as Zeus. In an email to your reporter from RSA’s Daniel Cohen in 2014, he wrote: “Waiting to see whether Kronos turns into something. At this point it’s just a post on a forum, no sample or binary yet. It could be an interesting development if it does, as it would point to more movement away from the Zeus code.”
But Kronos didn’t turn into much. In the last 24 months, according to IBM global executive security advisor Limor Kessem, the Trojan emerged with a hefty $7,000 price tag in mid-2014, but actual attacks didn’t launch until the third and fourth quarter of 2015, when the company saw some Kronos malware campaigns hitting UK banks. “But after that timeframe, have not seen much more activity from the malware,” Kessem told.
“The very last time we saw Kronos activity was a small campaign in November 2016, when Kronos infected a very small number of machines mostly in Brazil, the UK, Japan, and Canada. At that particular time, we did not see fraudulent activity from Kronos, but rather, believe it was used a loader for other malware.
“It never really took off in the cybercrime arena. It’s possible this was due to its pricing, its functionality, or the reputation of the vendors that peddled it in the underground and dark web markets.”
This would indicate that while Kronos may have claimed some victims, it never became anything close to a serious criminal operation. If the government is correct in its claim Hutchins was its creator, they may have a job on their hands proving it caused harm as the indictment alleges.
Legally speaking, the damage done and the intent behind it is critical to the government’s case against Hutchins and another unnamed suspect. From a two-year investigation, the feds revealed only one alleged sale of $2,000, not by Hutchins, but by the unnamed party. The indictment also claims the pair intentionally caused damage to 10 or more “protected computers” without authorization over a one-year period, with little more detail.
Tor Ekeland, a lawyer specializing in Computer Fraud and Abuse Act (CFAA) cases, described the charges as “a disaster”, claiming the government is trying to punish Hutchins for “non-alleged harms that other people may have committed with Kronos.” Hutchins is looking at two CFAA charges, one count of wiretapping and another three regarding the sale and advertisement of wiretapping devices.
“It’s like saying the gun manufacturer is now liable for the bank robbery or murder committed by a gun,” added Ekeland. “Who got killed with malware? No one, but it’s completely legal for someone to buy a gun.”
Beaumont, a highly-regarded malware researcher who knows Hutchins, said despite working in network defence for 17 years across four multinational companies, all with more than a billion dollars in revenue, he’d never heard of Kronos.


